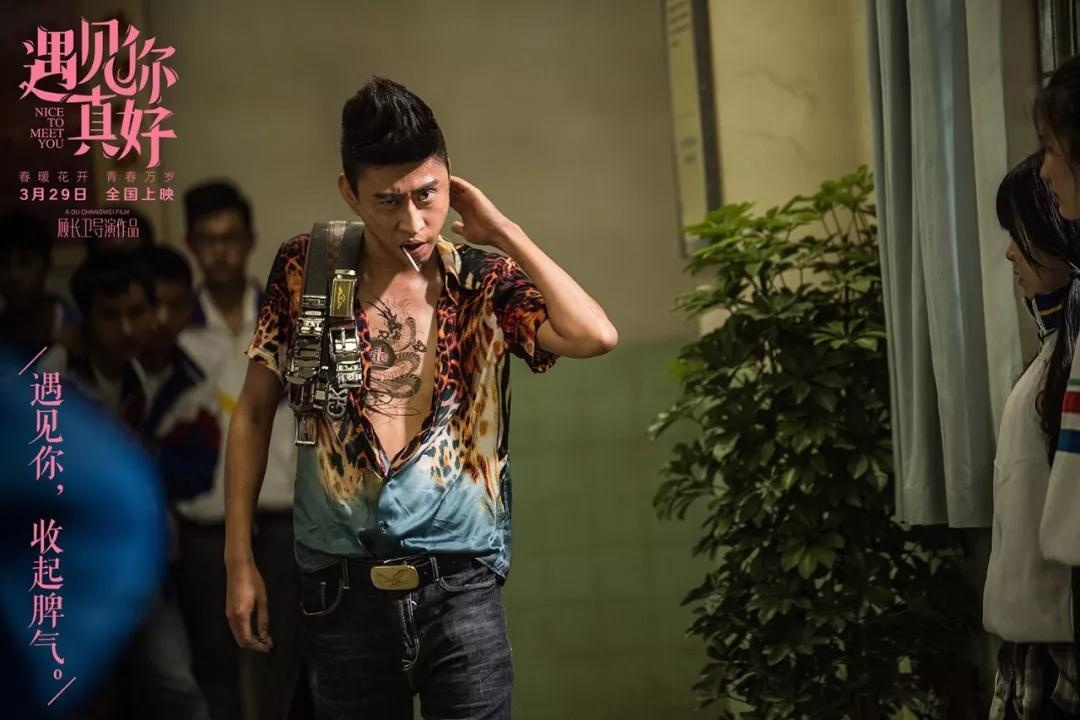Changwei Gu
Special feature of 1905 film network Gu Changwei has repeatedly expressed his recent original intention in interviews:
"My son is now 16 years old, and recently he seems to have a crush on a girl. My mood (facing him) is always very complicated. I have been observing his growth with curious eyes, but I don’t know how to talk to him (about youth). "
So, this one came into being.
The film "It’s good to meet you" is adapted from the novella "Flying to fireball" by young writer Kong Long, which tells the story of a group of repeat students in a special period — — The story of alternative youth and love that happened in senior four.
The film stars Ke Bai, Lyric, Zhang Haiyu, Chuchu Zhou, Cao Jun and other actors. Compared with Chen He and Angelababy in the previous film, this new film is a new actor. In the director’s words,"Let the audience focus on the content of the film."

"It’s good to meet you" poster
Now that the director has said so, let’s have a serious talk about the content.
Today, the film was officially released, and Douban scored only 5.1 points.

Of course, this is only the comprehensive score of netizens. It is hard for Xiao Dianjun to believe that Gu Changwei, who has made a film, can make such a film.
So, Xiao Dianjun went to the cinema for the first time to have a look.
The first impression is: Even though the douban score of the previous love on the cloud is only 4.6, Xiao Dianjun still thinks it is far better than this one, It’s good to meet you.

Although "love on the cloud" is extremely topical in casting, which inevitably leads to the black film in the end, the core essence of the film is still the routine that the director is good at — — The contradiction between literary dream and reality.
However, after "It’s good to meet you", the director uncharacteristically threw away the routines he was good at, and used online dramas, jokes and other forms to spell out a dish that was tasteless and even disposable.
The point is that it’s good to meet you, as a youth film, Gu Dao doesn’t understand the present youth.

Why do you say "present youth"?
After all, the film Peacock, in a way, is a youth film centered on Zhang Jingchu’s sister. However, it belonged to the youth of the 1970s and 1980s.

Gu Changwei’s Peacock
However, in the movie "It’s good to meet you", after this period of youth focused on modernity, Gu Changwei completely messed up.
Of course, some people say that this pot should not be directed by the director, but should be a matter for the screenwriter. Then let’s count the writers of this film first. In just 99 minutes, there are eight writers before and after, and director Gu Changwei is among them.

At the same time, in just 99 minutes, the story is presented in a three-stage form. So let’s make a bold guess here. Do you write a story for every 2-3 people, and then the main pen will save it together? Of course, this is just a guess.
Back to the film itself, the three-stage story — — It consists of three emotional stories of Ke Bai and Lyric, Zhang Haiyu and Chuchu Zhou, Cao Jun and Wang Yuwen.

Ke Bai and Lyric’s story, on the whole, passed, and even this story has a chance to be made into a feature film.
Except for the age mismatch between the actors and the movie characters, the overall situation is not too embarrassing.
After all, many people have time to write novels and have literary dreams in high school. It would be great if they could meet a girl.

However, when this story seems contradictory and the narrative is about to enter the first climax, the director suddenly stops the story and turns to tell the second story.
However, the second story is really terrible.

Once again, a key point is that the time background of the film takes place in senior four. What is senior four? It is to make up for the failure of the college entrance examination, and to struggle for the school major that I yearn for.
But in "It’s good to meet you", most of the time, you will have such a doubt, "Why don’t everyone study hard, but are flirting with girls?"

Moreover, in the second story, the image of each male is more "straight male cancer". Except for the central role played by Cao Jun, all the men revolve around the campus flower, fantasize about the story of themselves and the campus flower in the corner every day, and then "advertise" the imagined ugly story on the door panel of the toilet.
Cao Jun’s role as Ah Fu is more one-sided. Directly shaped into a silly boy who is incompatible with everyone, with a brute force to protect the campus beauty.

At the end of the second story, the punks were unwilling to be defeated by Ah Fu, so they burned down Grandpa Ah Fu’s restaurant with a firework.
However, in the last shot, there are still many students and waiters in the hotel who are reviewing. Is it because they are too serious about reviewing or too devoted to their work that they will not think about putting out the fire in the early days surrounded by smoke?
What is even more incredible is that a student was killed in the fire. Xiao Dianjun said that this group of senior high school students may need to learn fire prevention knowledge most.

Speaking of the third story, the whole is even crazier and completely irrational.
Chuchu Zhou’s boyfriend is the one who was burned to death in the second story. Therefore, at the beginning of this little story, she sadly wanted to jump off a building and commit suicide.
Seeing this, Xiao Dianjun is completely confused. Why are these students so irrational?

Gu Changwei once said in an interview,"Repetition will have stricter and more systematic management than schools, but it will also have some freedom. It will bring both middle school things and university things, including social things."
But now, by contrast, there is no so-called strictness in the film, and there is no social reason in it. Some are just the childishness of primary school students.

As a story that happened during the repetition period, besides the above-mentioned random settings, it is more important to make all the characters facelift.
No matter what period, the most memorable thing about student life is the surrounding students and teachers. But in "It’s good to meet you", the students in it are single-minded, even if they are single for dramatic effect, they can’t get any resonance from it.
Faceification of characters also exists in teachers.
The director teacher played by Fan Ming can be said to be a comedy, and he completely assumed the strict role of the teacher in everyone’s concept. But apart from being strict, it has no characteristics. So that at the end of the film, when the director of the teaching sensationally encouraged the students, there was no emotion at all.

At this point, you can completely compare movies. Similarly, Young Style tells a story about a repeat life, which also has emotional problems. But in the movie, Amanda plays the role of teacher, which can make a lot of audience stunned, pointing and shouting, this is my former class teacher!

Amanda’s Modeling in Young Style
Not only that, the students in the movies all have their own characteristics. Although they will also have a little exaggeration and facebook problems, you can directly feel that they are the epitome of every kind of classmates around you during your student days.

However, in "It’s good to meet you", such details are completely incomprehensible, and some are only: embarrassment.
The most embarrassing thing is that in the end, I don’t know if the movie designed a "local hip-hop" to increase the comedy effect.
If I have a chance to chat with Gu Dao, I really want to ask, do the eight writers of this youth film really understand youth?

Jiang Wenli’s role in this film is called "Wang Cailing".
And finally, I want to say, please stop consuming "Wang Cailing" from Gu Dao, after all, we will see the beloved Cai Ling again every year in beginning of spring.